Bypassing Facial Recognition — How to Detect Deepfakes and Other Fraud
In this article, we explain how fraudsters bypass facial verification and provide insights into choosing the most reliable anti-fraud solutions.
Since the dawn of facial biometric verification, fraudsters have been looking for ways to bypass it—from simple paper masks to sophisticated deepfake technology.
Deepfakes have been on the rise for the last several years, leading countries to tackle the spread of AI-generated accounts. In July 2022, the European Union planned to force tech companies to police manipulative accounts and content on their platforms. And in 2023, the EU announced the AI Act, which will separate artificial technologies into several groups of risks, as the EU believes they can be used for criminal purposes.
As deepfakes continue to spread like wildfire—along with increased regulatory scrutiny—it’s necessary for businesses to ensure that their facial recognition systems work flawlessly. That’s why we at Sumsub have prepared this article on the two main methods of bypassing facial recognition, along with tips on choosing the best face verification solution.
Method 1: Spoofing
When it comes to spoofing, there’s a wide range of technologies that can be used. Some of the most primitive ones include silicone masks—which, surprisingly, have been able to fool big tech companies over the years. However, nowadays, fraudsters are getting into more advanced forms of spoofing, including deepfakes. Let’s dive into each method.
Using pictures
In the era of social media, fraudsters can obtain almost anyone’s picture and use it to fool face verification. Therefore, if facial biometric technology does not analyze certain characteristics of an image, fraudsters can simply use social media images to hack devices and accounts.
Fraudsters can also use a similar method to gain access to people’s bank accounts. For example, a 34-year-old thief in Brazil managed to get access to several accounts and apply for loans by placing customer photos over a dummy.
Using video
You’d think that, if a verification technology asks users to make random movements like winking or blinking, it’s impossible to trick the system. Unfortunately, this isn’t really the case, as movements can be recorded in advance—and some verification systems fail to recognize such pre-recorded videos.
Using masks
There are silicone masks so realistic that it’s impossible to detect when a fraudster wears one. Criminals used this method to impersonate the French Defense Minister and were able to steal €55 million. They did this by phoning heads-of-states, wealthy businessmen, and large charities via Skype and claiming that they needed money to save people kidnapped by terrorists. Silicone masks can work if biometric technologies do not scan skin texture, blood flow, and the other characteristics.
Using deepfakes
Deepfakes use machine learning to either generate a fake persona or impersonate an existing person using manipulated photos and videos of them. A man in China recently sent $622,000 to a scammer after a video call that he thought was with his friend. At the moment, any industry working with customers on a remote basis is vulnerable to deepfakes.
Sumsub’s statistics show that the prevalence of deepfakes fraud grew considerably from 2022 to 2023:
- From 2022 to 2023, the proportion of deepfakes among all fraud types increased by 4,500% in Canada, by 1,200% in the U.S., by 407% in Germany, and by 392% in the UK.
- In Q1 2023, the most deepfakes came from Great Britain and Spain with 11.8% and 11.2% of global deepfake fraud respectively, followed by Germany (6.7%), and the Netherlands (4.7%). The U.S. held 5th place, representing 4.3% of global deepfake fraud cases
- Last quarter, a high proportion of fraud consisted of deepfakes in Australia (5.3%), Argentina (5.1%), and China (4.9%).
To put this in absolute numbers, from 2022 to 2023, the proportion of fraud consisting of deepfakes increased from 0.1% to 4.6% in Canada, from 0.2% to 2.6% in the U.S., from 1.5% to 7.6% in Germany, and from 1.2% to 5.9% in the UK.
Suggested read: Biometrics and the Fight against Criminals (Guide 2023)
Deepfake technology can easily be used to bypass facial recognition. Since everyone can create a deepfake at little to no cost with free generators, it’s easy to face-swap someone to gain access to their account. However, an efficient deepfake detection technology would be able to recognize deepfakes by analyzing artifacts on the provided image.
Method 2: Bypassing
Bypassing liveness does not include impersonation. Instead, fraudsters hack the liveness system itself by swapping in or editing biometric data.
Every liveness technology contains three weak points that hackers can target:
- The device on which the user undergoes the biometric check
- The internet connection on which the biometric data of the user reaches the server
- The server that checks the biometric data
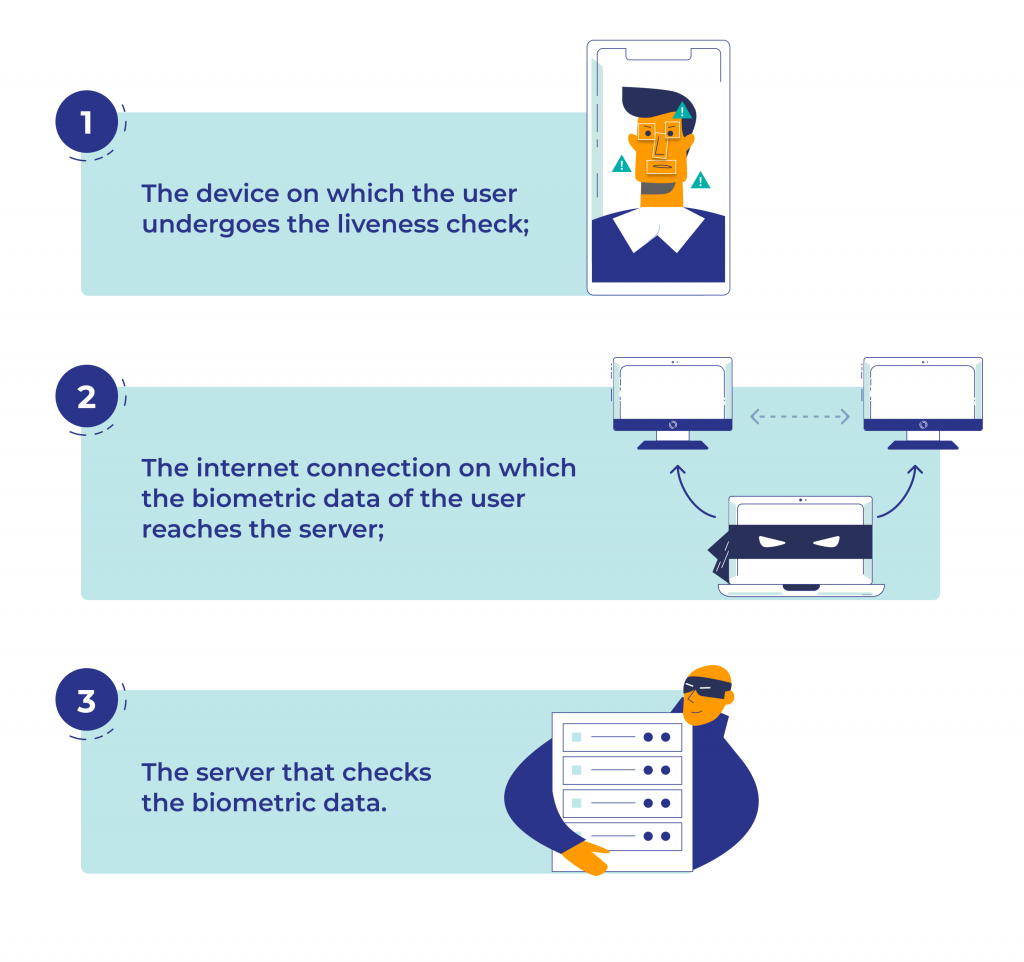
Fraudsters can take over a phone camera and inject a pre-recorded video or deepfake. Data transmitted over the internet can also be intercepted if it is not encrypted properly, and a server can be hacked.
Suggested read: Identity Theft Explained: How Businesses Can Detect and Prevent It
Tips on choosing hacker-resistant liveness
When selecting a biometric verification solution, companies should ensure that it protects against both spoofing and bypassing. Above all, it should differentiate between real faces and artificial objects, like deepfakes or pre-recorded videos. To do so, the solution must analyze parameters such as:
- Image depth
- Eye reflections
- Skin texture
- Blood flow
Face recognition can be performed within the verification suite’s interface, which is embeddable into other apps. It can be done via webcam, smartphone, and other camera-equipped devices. Usually, all you need to do is ask the user to move their head around while the system takes a number of photos (instead of a video) and analyzes each one for signs of spoofing.
The technology can be tested as follows
- Present a static image to the system
- Try to pass verification with eyes closed
- Use a face-spoofing prop, such as a mask, a deepfake, or a video
Any reliable technology should detect these fraud attempts.
It is also vital to ask the solution provider about the data encryption mechanisms that they employ, which should be state-of-the-art and resistant to replay or man-in-the-middle attacks.
Explore more
- Regulatory compliance
- Dec 21, 2023
- 10 min read
- Verification
- Dec 14, 2023
- < 1 min read





