Who Has the Best Security Measures? Top 3 Crypto Exchanges Compared
In this article, Scalable Solutions compares how the three biggest cryptocurrency exchanges—Binance, FTX, and Coinbase—cope with common security threats in their industry. The evaluation takes the form of a competition, with each firm earning a “cyber security coin” (CS coin) for every security measure it uses.
Cryptocurrency adoption has surged in recent years—as has related hacking and fraud.
In the first seven months of 2022, almost $2 billion was stolen in crypto through hacks, compared to just under $1.2 billion at the same point in 2021. So, how are leading crypto exchanges coping with increasing security threats? What security measures are taken and who does it best? Scalable Solutions is here to find out.
So let’s review and compare the security measures used by three biggest crypto exchanges : Binance, FTX, and Coinbase.
About the author:
Babar Ali. Head of Business Development MENA Region at Scalable Solutions.
Master of growth, strategic connections, and international expansion, Babar is actively spreading knowledge about cryptocurrency and blockchain technology adoption, as well as compliance and cybersecurity, advising governments of West-Asian countries, and helping organizations in the Middle East embrace the technology advancements of the digital asset space. Babar believes that security is what makes the digital asset business sustainable and predictable in the long-term.
About Scalable Solutions:
We have been developing institutional-grade white-label trading solutions since 2013. As a digital asset enabler and reliable technology partner, we work with dozens of clients all over the world, including those ranking in the top 20 crypto exchanges in CoinMarketCap’s global rankings.
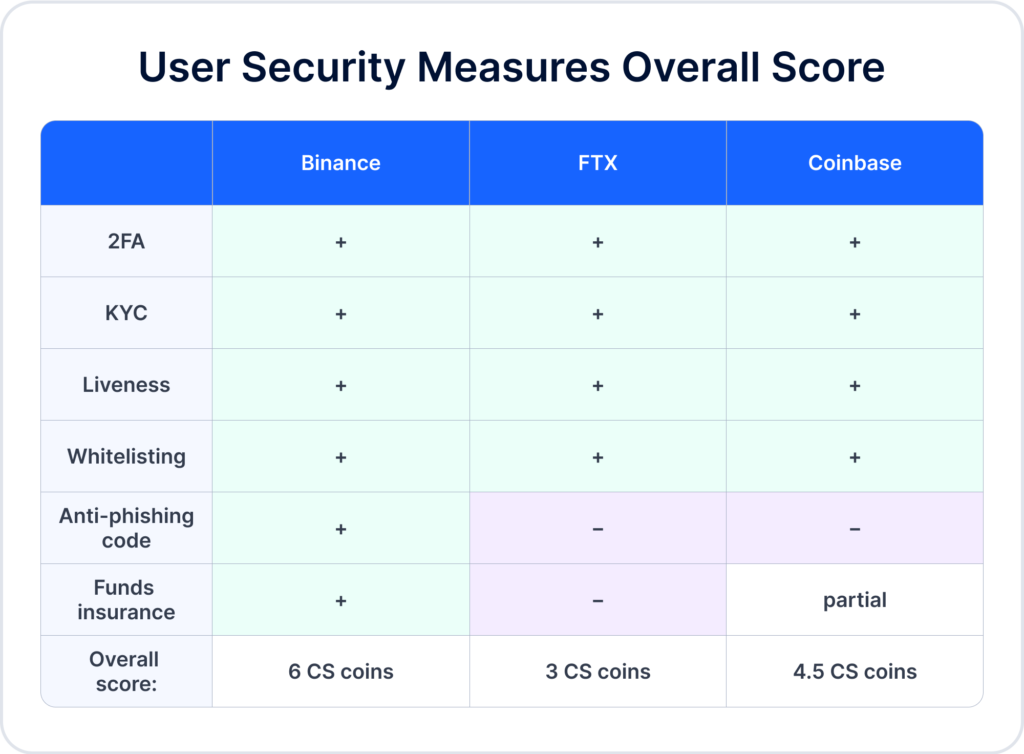
User security measures
Below, we list the security measures crypto exchanges usually apply towards users. If the exchange has implemented one of the security measures below, it earns one point. In the end, we’ll identify a winner.
Two-factor authentication (2FA)
This measure requires two of the following forms of identification from the user before granting access to their account.
- Something they know (password, PIN, or an answer to a secret question)
- Something they have (text code sent to your smartphone, or authenticator app, SMS code)
- Something they are (biometrics)
Results:
All three exchanges have 2FA.
KYC
Know Your Customer (KYC) is the process of identifying and verifying customers to prevent money laundering and other financial crimes.
To identify customers, businesses usually need at least the following information:
- name;
- date of birth;
- address.
To verify this data, companies require some documents and actions (like passing a liveness check) from customers. Required documents can include an ID card, driver’s license and/or proof of address (such as a utility bill).
Results:
All three exchanges apply KYC to their customers.
Liveness
Liveness is an advanced technology that utilizes biometrics to ensure that users are alive and present, rather than a presentation attack (paper mask, photo, doll, etc.). The system scans the applicant’s face, creates a 3D Face Map, and then applies deep-learning to discover intricate structures in the data. For the user, the process typically entails staring into a camera, performing certain movements or completing random tasks (such as pronouncing a few words), depending on what’s required by a given solution. It is a simple and user-friendly process that provides bullet-proof security.
Results:
- Binance uses liveness detection;
- FTX uses selfie verification, which is less secure than liveness;
- Coinbase uses liveness detection.
Whitelisting
A whitelist contains cryptocurrency addresses that users consider to be safe for transacting with. It allows crypto withdrawals only to authorized (whitelisted) wallets and to block transfers to unverified addresses.
Results:
All three exchanges have wallet whitelisting options.
Anti-phishing code
An anti-phishing code prevents phishing attacks. Once enabled, the code is included in all genuine emails sent from the crypto exchange, allowing to discern real emails from phishing emails.
Results:
- Binance has anti-phishing code.
- FTX doesn’t offer anti-phishing code.
- Coinbase doesn’t offer anti-phishing code.
Funds insurance
Funds insurance is paid out to users of an exchange to cover losses in the event of a security breach.
Results:
- Binance has Secure Asset Funds for Users (SAFU) valued at $1b.
- FTX doesn’t have funds insurance.
- Coinbase has funds insurance that covers a part of all cryptocurrencies stored. Its USD balances are FDIC-insured up to $250,000 per individual.
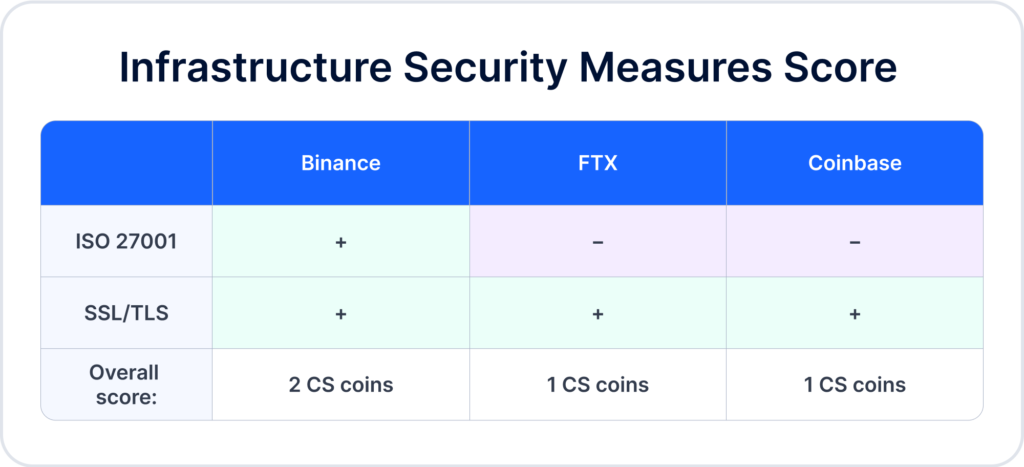
Infrastructure security measures
ISO/IEC Certification 27001
ISO/IEC Certification is an internationally recognized security standard. Any organization that is required or willing to improve information security and privacy may apply for this certification.
Results:
- Binance has ISO/IEC certification.
- FTX doesn’t have ISO/IEC certification.
- Coinbase doesn’t have ISO/IEC certification.
Secure Sockets Layer (SSL) / Transport Layer Security (TLS) certificates
SSL/TLS certificates are essential cybersecurity protocols that keep online transactions and logins secure through encryption. The SSL Labs Project grades security configurations from A+ to F. An A+ grade is given to servers with perfect security configuration quality.
Results
- Binance: A+
- FTX: A+
- Coinbase: A+
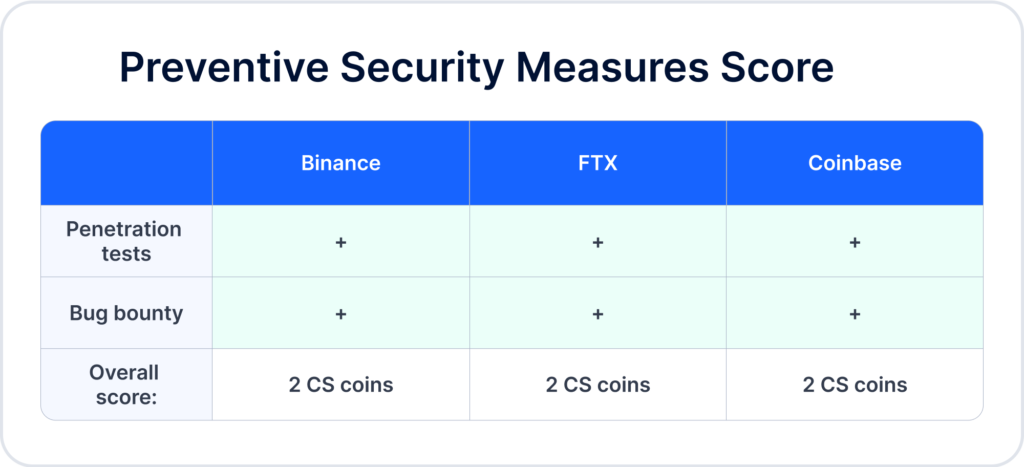
Preventive security measures
Penetration tests
Penetration testing are imitated cyber attacks that companies conduct on themselves to identify and resolve security vulnerabilities.
Results:
All three exchanges conduct penetration tests.
Bug bounty
The “bug bounty” program incentivizes ethical hackers to search for a platform’s vulnerabilities in exchange for rewards. This helps exchanges discover bugs before a possible cyber attack. It also creates incentives for hackers to report vulnerabilities rather than exploit them for illicit purposes.
Results:
All three exchanges have bug bounty programs.
Let’s calculate the overall amount of CS coins the crypto exchanges gained.
Overall Security Score
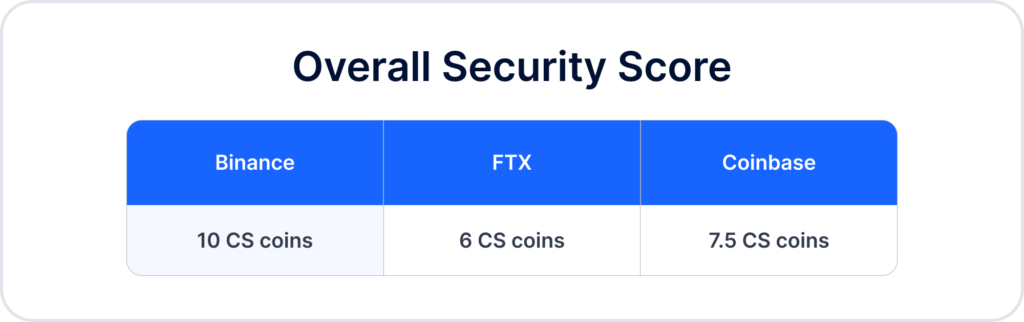
While all three exchanges appear to be taking security very seriously, we do have the winner, and it is Binance. This cryptocurrency exchange beats out the competition thanks to its ISO 27001 certification and anti-phishing code.
Conclusion
It’s not surprising to see major crypto exchanges pay so much attention to security. Having bulletproof security makes crypto exchange businesses considerably more successful in the long-term. And as technology evolves, so will the security measures to keep funds safe.
Want to know how we help our clients develop institutional-grade cryptocurrency exchanges and brokerages? Learn it from our customer success story: Achieving an Award-winning Brokerage for Institutional Traders.
Explore more
- Regulatory compliance
- Dec 27, 2023
- 6 min read






