How to Ensure Security When Using Blockchain
Learn about the most secure types of blockchain, best practices, and how to prevent hacks.
Blockchain technology can completely transform the way we interact online. But is it secure, given that cyber-attacks against blockchains have dramatically increased in recent years?
Which types of blockchain are considered the most secure, and what are the most frequent attacks against blockchains? Let’s break it down in this article.
What is blockchain? A quick recap
Blockchain is a digital distributed database which can be used to store and transmit data, often records of completed transactions. Organizations in different fields—from finance to healthcare—enjoy the benefits of blockchain.
In the blockchain, all records are presented in the form of blocks, which are interconnected by special keys. Each new block contains data about the previous one, which protects the chain from alteration.
Blockchain emerged in response to the issues we experience in Web 2.0 (the version of the internet that we currently use). Today users can lose their content easily, because centralized databases are vulnerable to hacks (your data can be accessed, forged and sold).
The emerging concept of Web 3.0—based on blockchain—is supposed to solve the main problems with Web 2.0. Web 3.0aims to become a peer-to-peer (P2P) network distributed between computers—from personal laptops to company servers. This way, information would be stored on multiple devices which participate equally in supporting the network.

Any service in need of a distributed database—which demands establishment of trust between participants—can enjoy the database integrity of blockchain. This can have impacts for a wide range of industries, from banking to digital identity.
Check out this detailed guide to blockchain and why it’s the future of the Internet: Blockchain, Digital Identity, and the Next Level of Data Security
Security on the blockchain
Blockchain technology is inherently secure because:
- It consists of a list of records which are united into blocks. Blocks are united to each other, and this connection can in no way be broken.
- Each blockchain participant can download the whole chain and personally check that the chain is mathematically correct and there has been no alterations to it.
- Blockchain features cryptography-based security.
Blockchain-based systems do not require direct exchange of information. Instead, digital data can be transferred and authenticated using cryptographic methods such as hashing functions.
Hashing algorithms ensure that any document can be converted into a hash—or a sequence of letters and numbers. This hash will contain all the information used to create it, acting as a digital fingerprint.
What’s important is that, once converted into a hash, personal information cannot be converted backwards. However, if two files need to be compared for authenticity, you can compare their hashes. This hash can also be published publicly, so that everyone could check that the data is not altered.
These are the basic security characteristics of blockchain technology. However, there are different blockchain types which differ in terms of security level.
Types of blockchains
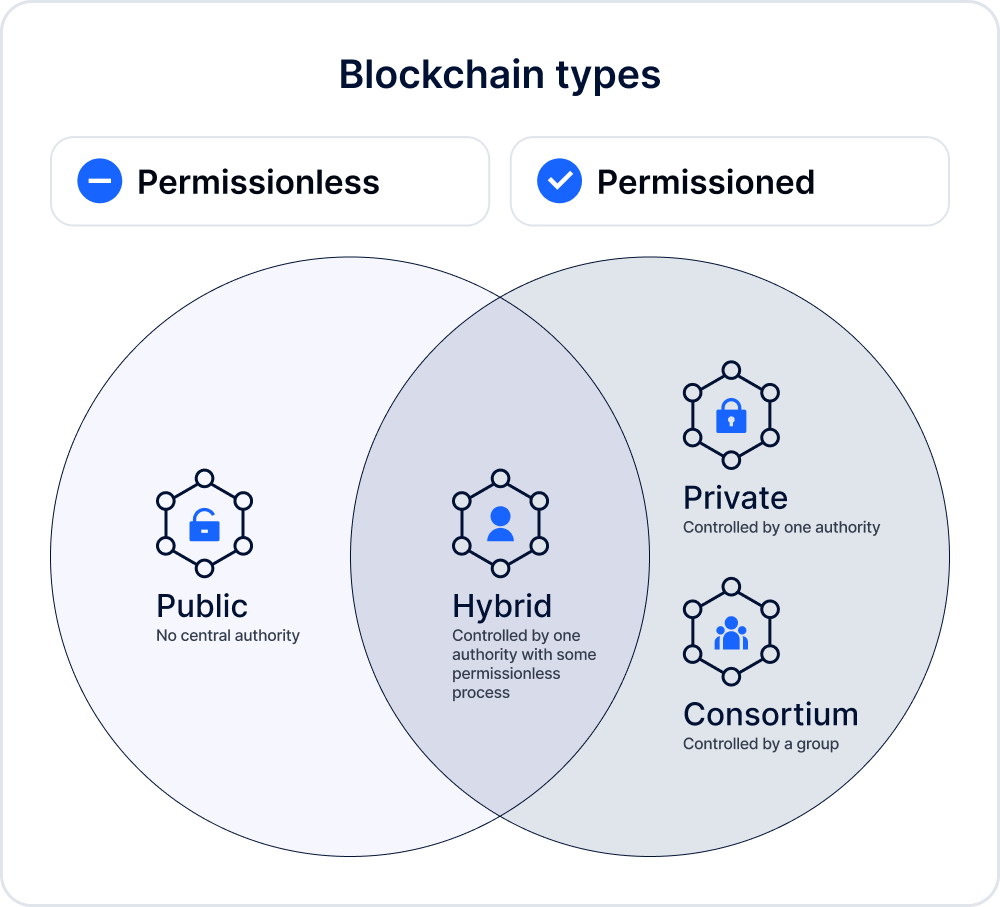
All blockchains can be divided into the following categories:
- Permissionless (public networks);
- Permissioned (private and consortium networks).
- Hybrid, which combines both.
Public blockchains
Public blockchains are permissionless, meaning anyone is allowed to create new blocks of data and validate them. Today they are mostly used to mine cryptocurrency. Bitcoin and Ethereum are the most well-known public blockchains.
On such blockchains, the participating computers, or nodes, “mine” for cryptocurrency by solving complex cryptographic equations in order to verify and add transaction records to the blockchain.
If the equation is solved successfully, the miner earns cryptocurrency, or a token, which they can use on an NFT or a crypto exchange.
Public blockchains are generally considered secure due to the decentralized nature of its ledger technology. However, there are still potential risks from malicious actors—for instance, a 51% attack, which we’ll discuss further later on.
Private blockchains
Private blockchains are a permissioned network managed by a single organization (node), which stores, tracks, and manages digital data while controlling access to the network.
Private blockchains are:
- more efficient than public blockchains due to their smaller network size and lack of competition for resources;
- more secure than public blockchains, because only approved members can join the network and access digital assets stored on it. To keep the network safe, its members follow cryptography and consensus mechanisms;
- less secure than consortium or hybrid blockchains, because of its centralized nature. Because there is only one controlling body, the whole network will be damaged if the governing body is compromised.
KitChain, MELLODDY Project, MyClinic.com are examples of private blockchains.
Consortium blockchains
Consortium blockchains (also known as federated blockchains) are also permissioned, but they differ from private blockchains because they have several selected participants (organizations) which control the network, while private ones have only one controlling node. Consortium blockchains are therefore more decentralized than private blockchains, which results in higher levels of security.
Federated blockchains can be used in scenarios where multiple parties need to come to an agreement on a shared set of data, i.e. finance, supply chain management, or Internet of Things (IoT).
Hybrid blockchains
Hybrid blockchains are controlled by a single organization, but validated by a public blockchain, which is required to perform certain transaction validations.
Blockchain security challenges
Any blockchain can become a target for hackers, both at the level of the blockchain code, and at the level of the protocols running on it. Examples include the Ethereum DAO hack, which led to the fork of Ethereum, or the recent BSC hard fork. At the same time, in case of a global attack, there is a chance that the blockchain community can take drastic measures to eliminate the consequences.
Although blockchain technology is considered inherently secure, it still has vulnerabilities including:
- 51% attacks
Blockchain can be altered if 51% of all nodes participating in the chain agree to an alteration. Bad actors can therefore conspire to form a 51% majority to commit harm. However, there are mechanisms to prevent such attacks and restore impacted networks. This attack is not possible with private blockchains.
- Sybil attacks
A Sybil attack is when a criminal tries to take over a blockchain by using multiple accounts, nodes or computers. It’s similar to the 51% attack, however in this case one person pretends to be multiple people to compromise the network.
- DDoS attacks
Distributed denial of service (DDoS) attacks involve multiple connected devices, known as a botnet, which are used to overwhelm a target website/network with fake traffic.DDoS attacks are hard to execute on a blockchain, but they’re possible.
When attacking a blockchain through DDoS, attackers intend to bring down the server by consuming all its processing resources with numerous requests from online devices. This is to disconnect the blockchain’s network’s mining pools, crypto exchanges, wallets, etc.
- Eclipse attacks
An eclipse attack is when hackers control a large number of IP addresses or have a distributed botnet. Then the attacker overwrites the addresses of the victim node and waits until the victim node is restarted. After restarting, all outgoing connections of the target node will be redirected to the IP addresses controlled by the hacker. The attacker may also use a DDoS attack to force the victim to reconnect to the network.
An eclipse attack can cause block mining disruptions and illegitimate transaction confirmations. There are ways to prevent eclipse attacks against blockchain.
- Race attacks
A hacker conducts a race attack when they create two transactions with the same amount at the same time in order to spend those funds twice. With this attack, hackers try to replace the first transaction with another one that returns the money to a wallet they control, prior to the first transaction being written on the blockchain.
- Finney attacks
According to Cryptopedia:
“A Finney attack is an attack where a miner pre-mines a transaction into a block from one wallet to another. Then, they use the first wallet to make a second transaction and broadcast the pre-mined block which has the first transaction. This requires a very specific sequence to work. This is only possible if the receiver of the transaction accepts an unconfirmed transaction.”
- Vector76 attacks
This attack combines Race and Finney attacks. Hackers create two transactions at the same time, and broadcast them to different parts of a network. The first transaction is of high value and is sent to the hackers’ address, and the second transaction is small. Attackers are credited with the high amount, while the second transaction eliminates the first transaction and gets the network’s final acceptance.
- Phishing
Phishing is a classic type of scam used to compromise users’ login credentials—including crypto wallet keys. Phishing emails may also contain malicious links compromising users’ credentials.
- Honeypot scams
A cryptocurrency honeypot scam is when a criminal creates a fake crypto wallet or token to convince their victims to send, invest, or trade crypto tokens. The scammer pretends to be a legitimate business and promises rewards or services, but in reality tries to steal cryptocurrency from their victim.
- Scam tokens
A scam token is a cryptocurrency that is created for the purpose of stealing investor funds. These are often developed on an existing blockchain, like Ethereum, Polygon, or Solana, as it’s easier for a cybercriminal to do this instead of creating an entirely new blockchain.
New crypto tokens emerge all the time. Some are legit, but many are outright scams run by criminals. There are ways to detect scam tokens, including researching developers, checking price history, etc.
The above scams aren’t the only ways criminals target blockchain. In 2022, for example, hackers stole $1.4 billion by hacking crypto bridges—technology that enables communication between different blockchain networks. DeFi protocols are another vulnerability hackers exploit. The most recent hack against DForce, an ecosystem of DeFi protocols, led to $3.6 million in damages. Therefore, any company looking to implement blockchain needs to keep the following security tips in mind.
Blockchain security tips and best practices
Our team has prepared a list of recommendations to help you stay secure when dealing with blockchains:
- Keep your credentials (mnemonic phrase and private key) secret. If your mnemonic phrase and private key are lost, you will never be able to restore the account.
- Check if the protocol you’re using has been audited. This may not guarantee 100% security, but will show you whether the contract owners are concerned about security.
- Check the result of transactions before sending them to the blockchain.
- Use transaction endorsement, which requires multiple parties to sign off on each transaction.
- Always be on the lookout for phishing attacks by using link checker tools and checking community reviews of unknown websites.
- Use a secure VPN.
- Use a secure crypto wallet like MetaMask (web / mobile), TrustWallet (mobile), or Ledger (physical device).
- Don’t use tokens of an unclear origin. These can cause you to lose control over your wallet
- If something seems like a honeypot, it probably is. Don’t trust it.
- Expect cyber threats around every corner.
FAQ
-
How does blockchain provide security?
Blockchain technology is inherently secure because:
- It consists of a list of records which are united into blocks. Blocks are united to each other, and this connection can in no way be broken
- Each blockchain participant can download the whole chain and check that the chain is mathematically correct and there has been no alterations to it
- Blockchain features cryptography-based security
- Blockchain does not require direct exchange of information. Instead, digital data can be transferred and authenticated using cryptographic methods such as hashing functions
-
Does blockchain have security issues?
Blockchain technology is secure, but there are some security issues which bad actors exploit.
-
Can a blockchain be hacked?
Yes. Although blockchain technology is considered inherently secure, it still has vulnerabilities which hackers can use. However, following blockchain cybersecurity tips can prevent cyber attacks.
-
How can blockchain be used in cybersecurity?
The cybersecurity industry enjoys blockchain’s unique security features, such as decentralization and its hash function. Among the most frequent uses of blockchain in cybersecurity are maintaining cryptocurrency integrity and improving government cybersecurity protocols.


![Crypto Regulations in Hong Kong [Updated November 2023]](index176f.html?url=https%3A%2F%2Fsumsub.com%2Fwp%2Fwp-content%2Fuploads%2F2023%2F02%2Fhong-kong-crypto-cover.png&w=768&q=75)


