NFC Chips and How You Can Use Them For Identity Verification
Over 80% of smartphones are now enabled with NFC (Near-Field Communication). As the technology grows in popularity, companies are exploring ways to implement NFC in their customer journeys.
In this article, we’re digging deep into NFC chips, their history, the pros and cons of NFC-based verification and the compliance issues that they raise.
Why should you read this?
To attract customers, businesses need fast, seamless, and remote onboarding processes. Otherwise, competitors will be able to quickly take advantage.
At the same time, more and more states are opting for chip-based ID documents to enhance security and prevent fraud. And it’s expected that the number of national eIDs, including chip-based IDs, will total 3.6 billion in 2021.
Therefore, there’s a rapidly-growing market for NFC-based ID verification, with many companies opting for this method. The question is, should you follow suit? And, if you do, what’s the best possible approach? Below, we’ll answer these questions.
What are NFC chips and how do they work?
NFC is a contactless technology that enables objects to communicate at a range of about 5 cm. Usually, one of these objects has an NFC-integrated circuit embedded (also known as a “chip”). The other is capable of reading the NFC chip. This allows communication between objects like payment terminals and payment cards or chip-based ID documents and smartphones.
The NFC chip combines with an antenna to form a self-contained, functional device—an NFC tag. The antenna allows the chip to interact with an NFC reader, such as a smartphone, by generating an electromagnetic field. NFC chips can use this field for the wireless communication of data.
The receiving device is given access to the sent data, as well as instructions on what it should do with it. For example, making a phone call, opening a webpage, storing data or establishing a data connection.
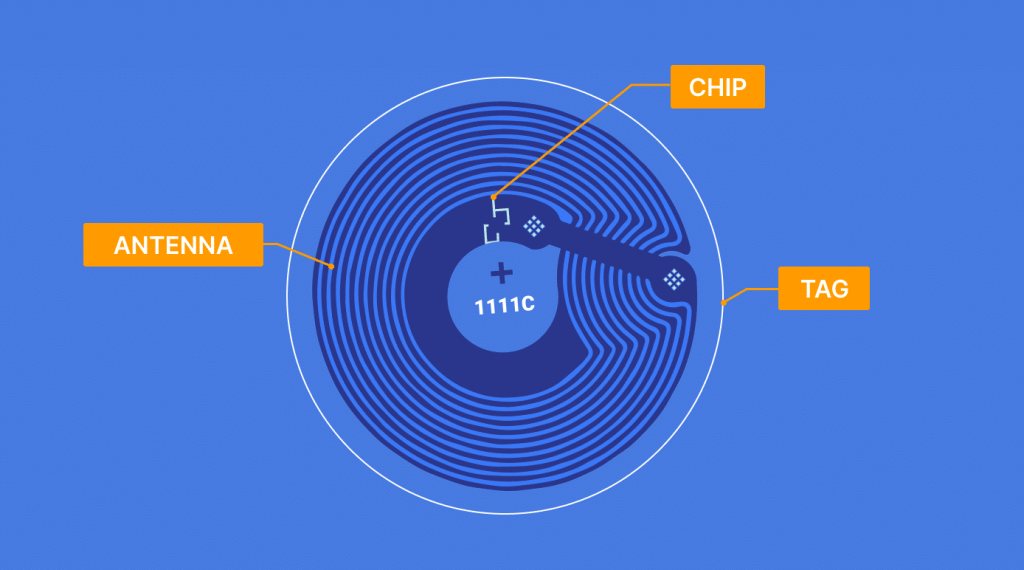
Here’s what an NFC chip looks like
What NFC chips are used for
NFC chips come in handy when a few bits of digital information need to be exchanged. The applications of this technology are practically limitless, but some of the main ones are:
- Connecting wireless components to a desktop or mobile device;
- Accessing digital content by using an NFC-reading device—like a smartphone—to read a “smart” poster;
- Making contactless transactions, including those for payment and ticketing.
NFC chips can engage consumers in various ways. That’s why brands are starting to use them to deliver more personalized and interactive customer experiences. This is also true for the identity verification industry.
NFC chips and identity verification
This method authenticates customer identities through chip-based identity documents. These documents contain Radio Frequency Identification (RFID) chips that store personal information, such as name, date of birth, address, and sometimes even biometric information. NFC-enabled devices can read RFID data, which makes this sort of verification possible.
NFC-based verification leverages two things everybody has—IDs and smartphones. By tapping an NFC-enabled device against the ID, the RFID data within the NFC chip is extracted and verified (by cross-referencing the information printed on the ID document).
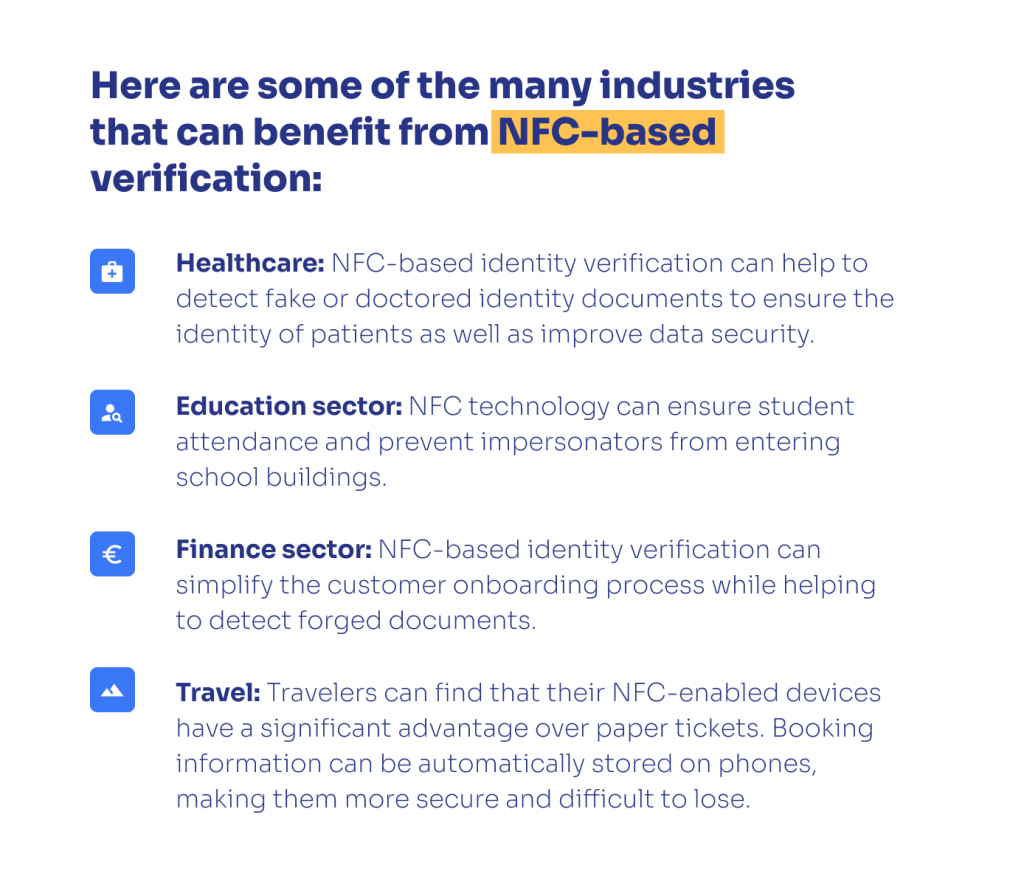
The healthcare, travel, education and finance sectors are among the many sectors that can benefit from NFC-based verification
The optimal verification process
Here’s our practical advice for building an effective NFC-based solution.
Step one
Businesses can integrate a ready-made app (prescribed by regulators or developed by specialized third-parties) to read NFC chips and then use their own software to perform all kinds of verification. At Sumsub, we’ve integrated an NFC reading system into our Mobile SDK.
Step two
Businesses need to build a separate verification flow for users that have chip-based IDs and phones capable of reading NFC. The verification flow might look like this:
- A user takes a photo of their documents;
- The verification system detects whether both the user’s phone and ID document support NFC;
- If they do, the user needs to simply tap their phone against the ID;
- The verification system extracts the data (name, document number, and issue date) from the NFC chip in the document and cross-checks it with the same data extracted from the picture.
For other users, businesses need a separate verification flow. This can, for instance, include document screening and face authentication.
Onboard users securely with Sumsub’s NFC-based verification. Request a demo today.
Pros and cons of NFC-based verification
Advantages
NFC-based identity verification provides a range of benefits to consumers and businesses.
- It’s simple: NFC interactions require no more than the tap of a device and a document, providing an intuitive user experience. Today, NFC is available as a standard functionality in many mobile phones. So the same NFC chip that allows for mobile payment also empowers mobile identity verification.
- It prevents fraud: NFC can detect forged documents and fraudsters in real-time. The chances of onboarding fraudsters diminish, making it easier for companies to comply with regulations.
- It’s secure: Data can be read directly from an ID document chip. Since these chips can’t be tampered with, businesses can securely onboard legitimate customers by validating all the data within them. However, it’s important to note that mobile phones are vulnerable to hacking.
- It’s fast: NFC speeds up transactions and the customer validation process, boosting efficiency and customer acquisition rates.
However, everything has its drawbacks.
Disadvantages
Despite increased security, speed, and convenience, there are some things one should be wary of:
- It’s pricey: Like any advances in technology, there are costs attributed to development and implementation. Due to its high costs, the introduction of chip-based ID documents is likely to be limited to wealthier jurisdictions.
- It’s unfamiliar: NFC-based verification is still a relatively new technology. Many people don’t know what the technology is and wouldn’t immediately trust its security.
Before you go ahead and opt for NFC identity verification, you should consider these pros and cons. Businesses might need major improvements to introduce it, including, but not limited to, compliance-related updates.
Compliance challenges
Below, you’ll find a list of the key challenges for client onboarding when using NFC-based verification.
Privacy issues
If NFC-based verification is approved by a jurisdiction, then, as a rule, the company using this authentication method must follow local data protection laws. These can be both general data protection laws, as well as special ones aimed at regulating relations in the field of information technology. Here’s an example of the GDPR.
The EU GDPR is technologically neutral, which means that all personal data will be protected regardless of the technology used for their recording or conservation.
Moreover, according to Article 25, “Data protection by design and by default”, the producers of the products, services, and applications, which will process personal data, shall integrate the data protection system into the product or service at an early stage of the design.
In addition, they shall set the settings for maintaining confidentiality by default. That is, the user doesn’t need to take any action to protect their privacy.
Additional steps
No matter which method of data collection you’re using, there’s an identity checking procedure you should follow to stay compliant. Accordingly, there are multiple steps to an effective AML compliance program, including document and PEP checks, face matching, and so on. NFC-based verification is only one of these steps, so it will need to be combined with others to ensure total compliance.
Jurisdictions with additional requirements:
The UK. According to guidance on how to prove and verify someone’s identity with NFC, you can only prove that an identity exists by collecting digital evidence and validating it.
This requires checking the following:
- That the claimed identity has existed over time, hasn’t been canceled, expired, reported lost or stolen;
- That the identity belongs to the person who’s claiming it;
- Whether the claimed identity is at high risk of identity fraud.
Turkey. The Regulation on Verification Process of the Applicant’s Identity in the Electronic Communications Sector permits NFC-based verification. However, in this case, businesses must conduct a video conference with a customer and confirm their contact information by sending a single-use password or link to the user’s mobile number or e-mail address.
Special app usage
As a rule, reading NFC chip data is only possible with a special app. These apps may be issued by regulators or third-parties.
Examples:
- The Swiss Financial Market Supervisory Authority, FINMA, requires a special mobile app for reading chip data;
- The German government’s AusweisApp2 enables consumers to use public services, open a customer account, or submit a funding application, as well as securely identify themselves to an online service provider;
- The French “Alicem” smartphone app is designed to securely authenticate citizens using NFC passport readings to any of the 500-plus services available via FranceConnect, a government-backed online services gateway used by government agencies and private-sector companies.
This isn’t a complete list of applications, jurisdictions and requirements. Overall, compliance challenges are rapidly increasing, and we’ll constantly update them in this article.
End note
The need for high-quality KYC processes is becoming more pressing than ever before. In-person transactions are becoming a thing of the past, and we need advanced solutions to facilitate the move to digital alternatives. This means implementing new technologies, which are emerging day by day.
But, with any new technology, implementation is only half the battle. Businesses also need to be prepared for possible compliance challenges.
Stay tuned to our blog for more news and tips from our compliance experts.
Explore more
- Regulatory compliance
- Dec 21, 2023
- 10 min read
- Verification
- Dec 14, 2023
- < 1 min read





